Data Security At Microkeeper
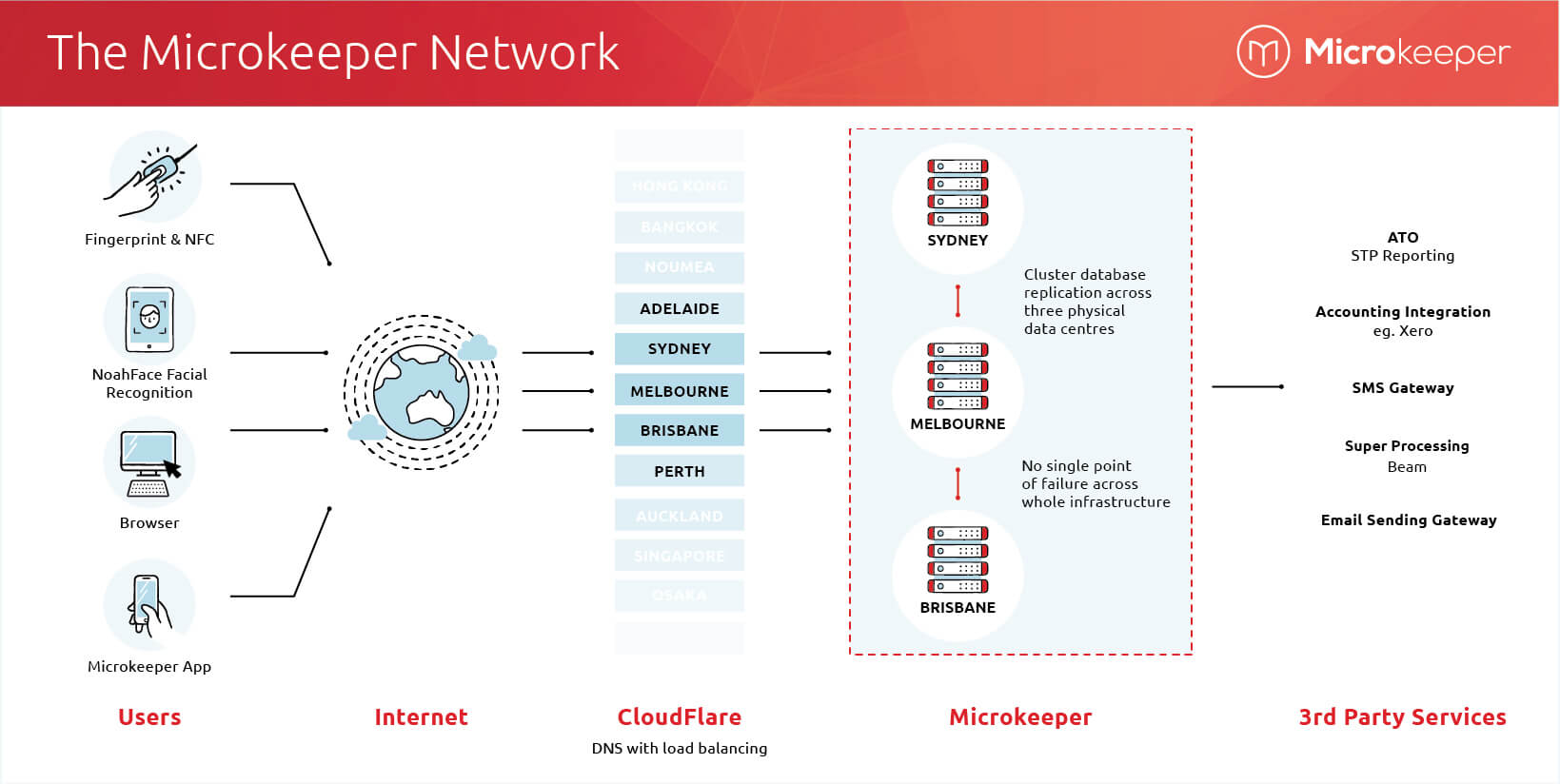
Microkeeper Network and Infrastructure Design
Data Sent To Third Parties
Microkeeper integrates with many third-party software providers, these providers have access to different levels of data depending on what is required to achieve the desired outcome.
These providers do not have access by default, the accounts administration must trigger an action to these providers for the data to be forwarded.
Here is a list of third-party software providers and the data they have access to:
| Software Provider | Access Level | Reason | Data Access |
| Beam | High | Process Super | Name, DOB, TFN, Mobile, Superfund, Member number, Super contribution values |
| ATO | Very High | Submit Single Touch Payroll | Almost all fields |
| Twilio | Low | Send SMS | Name, Mobile |
| Apple | Low | Send Push Notifications | App device token |
| Google Apps | Low | Send Push Notifications | App device token |
| NAB Merchant facility | Medium | Make Credit Card Payments | Credit Card Details, Username |
| Xero | Medium | Send Invoice for Payroll | Accounts, Cost of wages, PAYG values, Super values |
| NoahFace | Medium | Clock hours via facial recognition | Employee user list: Name, email |
| Hubspot / Freshdesk | Low | Sales and support CRM and tickets | Email, mobile number, ticket/email content, contact name |
| vSure | Medium | VEVO Checks | Passport number, name and country |
Microkeeper Fingerprint Data Retention
An image of the fingerprint is not stored. The fingerprint is converted to a binary string.
Below is my fingerprint and how it looks as a binary string:
123C2A062123C2A062E123C2A062E296B2912 3C123C2A062E296B2123C2A062E296B299123C2A062E296
B292A062E296B292123C2A062E296B2996B29 123C2A062E2123C2A062E296B2996B29E2123C123C2A062
E296B292A123C2A062E296B29123C2A062E29 6123C2A062E296B29B29062E296B2962E296B2962E96B29
This string can not be converted back into a fingerprint and is only useful to the Microkeeper fingerprint interpreter.
ISO 27001:2022 Compliant

Microkeeper is ISO 27001:2022 which is globally recognized as the premier Information Security Management System (ISMS) standard.
Compliance is a requirement of SBR and is permitted to submit STP data, verification of Microkeeper can be found on the Standard Business Reporting Product Register.
Verification of Microkeeper's ISO 27001 compliance can be found on the jas-anz website.
View Microkeeper ISO 27001 Certificate
Best in Class Infrastructure
Microkeeper delivers best-in-class availability. Microkeeper uses multiple redundancy technologies for our servers, networks, databases, and data.
These ensure that if any component fails, Microkeeper will recover with little or no disruption to your service or loss of data.
SLA Guarantee
Microkeeper guarantees at least 99.9% availability of our cores services.
This does not include:
- Maintenance windows
- Features that require third party services, eg processing Super.
- Hardware
- User ISP connections
Server Hosting Environment
Microkeeper has co-location hosting across Sydney, Melbourne and Brisbane.
Microkeeper uses different server hosting environments for different parts of the system stack.
All hosts are in Australia and highly critiqued by the Microkeeper Engineering team.
All hosts have:
- Best in class infrastructure
- High uptime
- High-security standards
Our servers are in the Equinix data centre, Equinix are also ISO 27001 compliant.
DNS and Load Balancing
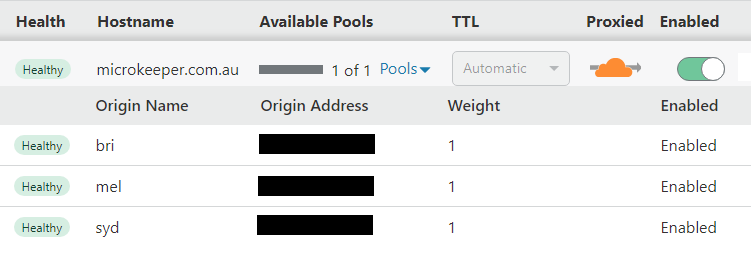
Microkeeper uses CloudFlare for our DNS and Load Balancing, this allow for user requests to be shared across multiple physical location.
The CloudFlare status page can be reviewed to help debug connectivity issues.
In the event that one of the three physical data centres goes completely down, Microkeeper service will remain available.
Disaster Recovery
Microkeeper has internal Disaster Recovery policies and procedures.
This documentations covers events like:
- Server hardware failure
- Data breaches
- Network connection issues
- Database data loss
- And dozens of other mission critical event
Disaster Recovery documents are reviewed every 12 months or when a major release of Microkeeper is moved to production.
Cluster Database
Microkeeper uses a cluster database technology that synchronizes data between all servers in the cluster in real time.
If a database server goes down, the other servers will take over with almost no interruption to the user and no loss of data.
When the server that went down comes back up, it re-joins the cluster, receiving any changes to the database that it missed.
Firewalls
Firewall upkeep and maintenance is a joint responsibility of our server hosts and Microkeeper admin team.
Visit the Equinix website for more information about their data security policies.
One of the benefits of CloudFlare is they have DDOS protection built in and server anonymity, so server whereabouts is not known to the public.
Anti-Virus Policy
AV is not required for the hosting environment, this is because it's a locked-down environment, where new software vendors are only installed once they have been tested in a production environment.
In house all Support and Software Developer run Windows Defended, updates are fully automated.
Software Update Policy
Third-party vendors are updated as new releases, where possible automated updates are implemented.
Where automated updates are not possible, manual installation is conducted.
Manual updates typically take between a few days to a couple of weeks depending on risk profile and difficulty of implementation.
Data Retention Policy
Microkeeper has a "No Print Policy" thus no customer data is ever printed.
Data is kept for a minimum of 10 years in alignment with Australia Law.
If an account parts way, Microkeeper retains data.
Microkeeper reserves the right to delete data once it is 10 years old via built-in scripts.
Backup Policy
An automated backup is taken during quiet times on a daily basis.
An Annual backup is taken which is kept indefinitely.
9 backups are kept for 9 days.
Backups are encrypted with AES-256 encryption at rest (including disk-level encryption) and TLS 1.3 / 256-bit SSL in transit.
Password Policy
Microkeeper requires the following for a strong password:
- Must be 8 or more characters long
- Must contain upper and lower case characters
- Must contain at least 1 number
- Must contain at least 1 special characters
Account lockout is for 5 minutes after 5 attempts at a password.
After a maximum of 50 attempts the account is permanently locked and can be unlocked by contacting admin.
When storing passwords in the database, they are hashed using sha256 and a proprietary double salting.
Microkeeper internal password policy is much stronger, passwords are randomly generated and we use password managers.
Session Management
Microkeeper uses encrypted session cookies to maintain user authentication. Session data is encrypted using AES-256 encryption and stored in HttpOnly cookies to prevent cross-site scripting attacks.
Session Timeout:
- Sessions automatically refresh every 20 minutes while Microkeeper is actively being used
- Active sessions expire after 2 hours if no user input is detected
- Inactive sessions expire after 30 minutes if the browser is closed
Session tokens are validated on every request and expired sessions are immediately invalidated. Session timestamps prevent replay attacks.
Multi-Factor Authentication (MFA) Session Management
When MFA is enabled, users must complete Multi-Factor Authentication verification.
Trusted Device Recognition:
After successfully completing MFA verification, the device is recognised as "trusted" and can skip MFA verification for 90 days from the last successful login.
Each device receives a unique, encrypted token. If you log in from a new device, you will need to complete MFA verification again.
MFA Token Management:
- MFA tokens are encrypted and stored securely
- Tokens are device-specific and validated against a secure database on each request
- When logging in from a trusted device, the MFA token is automatically extended for another 90 days
- Tokens expire automatically after 90 days of inactivity
- The system limits MFA verification attempts to prevent brute force attacks
Audit Logs
There are many different audit logs
Activity Feed
Microkeeper has an Activity Feed that logs changes that are made within the Microkeeper software.
Account Access
Account access is logged this includes externally Linked Users and Microkeeper staff.
Production Server
Only Microkeeper directors have access to production servers.
Events are recorded when production servers are accessed.
Multi-Factor Authentication is setup on all production servers.
Audit logs are reviewed monthly for suspicious activity, alongside automatic email notifications when particular events are triggered.
Production server access log example:

Domain Segregation
Microkeeper uses cloud services for all internal file and data sharing tasks, this means all staff devices have internet only access, there is no file sharing setup on internal networks.
This means segregation is controlled at the application or session layer not the network layer.
Encryption - Data In Transit
All data sent to and from Microkeeper servers is done via a 256-bit SSL encrypted connection, this can be verified within browser near the URL.
Encryption - Data At Rest
Some values are encrypted at rest and some values are not, for example, TFN is encrypted.
Microkeeper does not encrypt all fields, this is because it can hinder database performance and slow down search queries.
Which fields Microkeeper encrypts and which ones Microkeeper does not encrypt is proprietary and will not be disclosed.
Bug Bounty
Microkeeper encourage ethical hacking to help identify bug early and reward those who participate.
We have an official Bug Bounty Program, which anyone from around the world is welcome to explore.
Secure SDLC (Security by Design)
Microkeeper embeds security into every phase of the software development lifecycle, aligned to NIST and OWASP practices.
Changes are reviewed, tested, and validated before production release.
Application Security Testing (SAST & DAST)
Microkeeper run automated Static (SAST) and Dynamic (DAST) security testing to proactively identify vulnerabilities.
Findings are remediated and re-verified prior to production deployment.
Penetration Testing & Vulnerability Management
Microkeeper undertakes regular vulnerability scanning and an annual penetration test.
Pen test reports are not distributed externally because they may contain information about exploits.
Last Penetration Test: October 2025
Business Continuity & DR Testing
Microkeeper maintains documented BCP and DRP processes.
Detailed BCP/DR documentation is not distributed publicly as it contains sensitive implementation details around operational security.
Production Access Controls (Least Privilege)
Production server access is restricted to directors only, protected by MFA, and access events are logged and reviewed monthly.
Environments & Customer Data Separation
Microkeeper operates three environments:
- Local development
- Beta Testing
- Production Cluster
Only production contains customer data, reducing exposure risk during development and testing.
Customer data can only be accessed via the Microkeeper application, no direct database access is available.
Security Monitoring & Misuse Detection (KYC Controls)
Microkeeper has real-time monitoring triggers that generate alerts when potential misuse of features is detected.
This forms part of Microkeeper's broader KYC framework for proactive risk management and compliance oversight.
Incident Response & Customer Notification
Microkeeper maintains a formal incident management process covering identification, containment, recovery, and post-incident review.
Customer notification timeframes depend on severity, with a target of as soon as possible, ideally within 48 hours where feasible.
Third-Party Risk Management (TPRM)
Microkeeper applies a Third-Party Risk Management approach for critical suppliers, including due diligence and ongoing review, to ensure supply-chain partners meet documented security expectations.
AI Use Policy (Customer Data Safety)
Microkeeper may use AI to assist support workflows.
Customer data handling remains governed by the ISO 27001:2022 ISMS and is not used to train AI.
A best effort is made to remove PII before data is sent to an AI service.
Note
The details in this document are a brief summary of more extensive internal documentation and are not legally binding.
For a more detailed explanation please review the Microkeeper Privacy Policy and Terms Of Use.
If you require further clarification on anything in this document please Contact Us.
Last Updated
12/02/2026